Tomcat is one of the most popular Servlet and JSP Container servers. It’s used by some of following high traffic websites:
LinkedIn.comDailymail.co.ukComcast.netWallmart.comReuters.comMeetup.comWebs.com
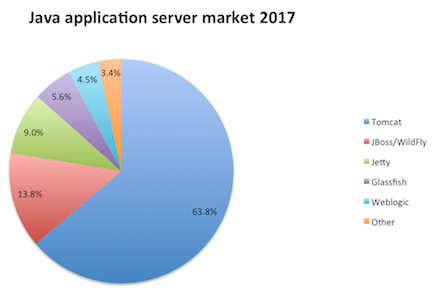
Below chart shows the market position of Tomcat in the Java application server. Technically, you can use Tomcat as a front-end server to serve site requests directly. However, in a production environment, you may want to use some web servers like Apache, Nginx as front-end to route the requests to the Tomcat. Using a web server to handle the requests gives performance and security benefits. If you are using Apache HTTP as a front-end web server, then you must consider securing that as well. Having default Tomcat configuration may expose sensitive information, which helps hacker to prepare for an attack on the application. Following are tested on Tomcat 7.x, UNIX environment.
Audience
This is designed for Middleware Administrator, Application Support, System Analyst, or anyone working or eager to learn Tomcat Hardening and Security. Good knowledge of Tomcat & UNIX command is mandatory.
Notes
We require some tool to examine HTTP Headers for verification. There are two ways you can do this. If testing Internet-facing application, then you may use the following HTTP Header tools to verify the implementation.
HTTP Header CheckerHacker Target
And for an Intranet application, you may use Google Chrome, Firefox developer tools. As a best practice, you must take a backup of any file you are about to modify. We will call Tomcat Installation folder as $tomcat throughout this guidelines. Let’s go through the hardening & securing procedures.
Remove Server Banner
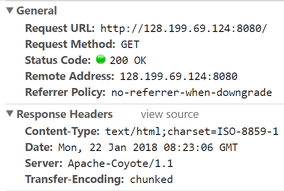
Removing Server Banner from HTTP Header is one of the first things to do as hardening. Having a server banner expose the product and version you are using and leads to information leakage vulnerability. By default, a page served by Tomcat will show like this. Let’s hide the product and version details from the Server header.
Go to $tomcat/conf folderModify server.xml by using viAdd following to Connector port
Ex: –
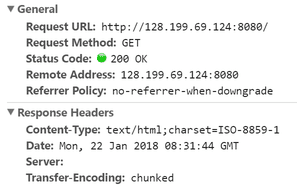
Save the file and restart the Tomcat. Now, when you access an application, you should see a blank value for the Server header.
Starting Tomcat with a Security Manager
Security Manager protects you from an untrusted applet running in your browser. Running Tomcat with a security manager is better than running without one. Tomcat has excellent documentation on Tomcat Security Manager. The good thing about this is you don’t need to change any configuration file. It’s just the way you execute startup.sh file. All you got to do is to start tomcat with –security argument.
Enable SSL/TLS
Serving web requests over HTTPS is essential to protect data between client and Tomcat. In order to make your web application accessible through HTTPS, you need to implement SSL certificate. Assuming, you already have keystore ready with the certificate, you can add below line in server.xml file under Connector port section. Change the Keystore file name and password with yours. If you need help with the keystore & CSR process, then refer to this guide.
Enforce HTTPS
This is only applicable when you’ve SSL enabled. If not, it will break the application. Once you’ve enabled SSL, it would be good to force redirect all HTTP requests to HTTPS for secure communication between user to Tomcat application server.
Go to $tomcat/conf folderModify web.xml by using viAdd following before syntax
Save the file and restart the Tomcat
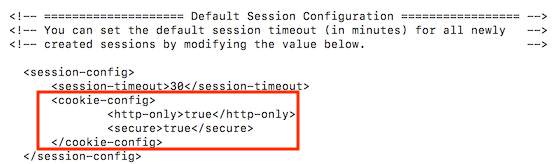
Add Secure & HttpOnly flag to Cookie
It is possible to steal or manipulate web application session and cookies without having a secure cookie. It’s a flag which is injected in the response header. This is done by adding below the line in session-config section of the web.xml file Configuration screenshot: Save the file and restart Tomcat to examine the HTTP response header.
Run Tomcat from non-privileged Account
It’s good to use a separate non-privileged user for Tomcat. The idea here is to protect other services running in case of any of account get compromised.
Create a UNIX user, let’s say tomcat
Stop the Tomcat if runningChange $tomcat ownership to user tomcat
Start the Tomcat and ensure it’s running with tomcat user
Remove default/unwanted Applications
By default, Tomcat comes with following web applications, which may or not be required in a production environment. You can delete them to keep it clean and avoid any known security risk with Tomcat default application.
ROOT – Default welcome pageDocs – Tomcat documentationExamples – JSP and servlets for demonstrationManager, host-manager – Tomcat administration
They are available under $tomcat/webapps folder
Change SHUTDOWN port and Command
By default, tomcat is configured to be shutdown on 8005 port. Do you know you can shutdown tomcat instance by doing a telnet to IP: port and issuing SHUTDOWN command? Dangerous! You see, having default configuration leads to high-security risk. It’s recommended to change tomcat shutdown port and default command to something unpredictable.
Modify the following in server.xml
8005 – Change to some other unused port SHUTDOWN – Change to something complicated Ex-
Replace default 404, 403, 500 page
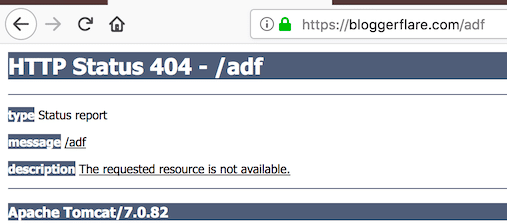
Having default page for not found, forbidden, server error exposes version details. Let’s look at the default 404 page. To mitigate, you can first create a general error page and configure web.xml to redirect to a general error page.
Go to $tomcat/webapps/$applicationCreate an error.jsp file using vi editor
Go to $tomcat/conf folderAdd the following in the web.xml file. Ensure you add before syntax
Restart tomcat server to test it
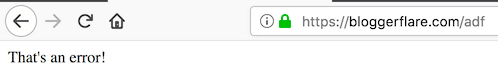
Much better! You can do this for java.lang.Exception as well. This will help in not exposing tomcat version information if any java lang exception. Just add following in web.xml and restart tomcat server. I hope the above guide gives you an idea of securing Tomcat. If you are looking to learn more about Tomcat administration, then check out this online course.Also, learn how to configure WAS to stop asking for password during shutdown here.